PRWeb – RunRev Launches First Kickstarter Campaign for an Open Source Programming Language, Empowering Everyone to Code
by Jana Doughty on January 29, 2013 No commentsmac4ever – L’outil de développement Livecode bientôt en open source ?
by Jana Doughty on January 29, 2013 No commentsHeise – Entwicklungssystem LiveCode soll Open Source werden
by Jana Doughty on January 29, 2013 No commentsTNW – RunRev launches Kickstarter campaign to create open source version of LiveCode
by Jana Doughty on January 29, 2013 No commentsSecuring Your Data on iOS
by Arnaud on January 25, 2013 No commentsby Mark Smith
Mark Smith manages the data repository at the Manitoba Centre for Health Policy and conducts health research. In his spare time he codes medical and other kinds of applications using LiveCode.
______________________________________________________________________________________________
If you have sensitive information that needs to be secured on an iOS platform then you may find the following discussion useful. Such was the case for a hospital application I was developing that required the collection of personal health information. Not surprisingly the client was only willing to consider a mobile option if the information could be securely stored and managed on the device as well as off. And, unfortunately, storage on the device was the only option since the hospital had neither 3G nor wireless available (which would have allowed a mobile client/server solution).
Securing data on iOS is not as easy as it sounds. If you provide no more protection than a simple 4-digit numeric passcode, then this can easily be defeated. There are desktop applications that can be downloaded that can brute-force discover any 4-digit numeric code in under 20 minutes. Things get a little better if you use a more complex passcode and you can enforce the requirement of a complex passcode by creating a configuration profile for your device (more on that in a bit).
So I was really pleased to see that RunRev had implemented support for the hardware based encryption that is built into iOS through the Data Protection API in version 5.5 of Livecode. As noted in the LiveCode documentation, there are four options available for the iphoneSetFileDataProtection command:
- none – No protection
- complete – The file is not accessible, for reading or writing, while the device is locked.
- complete unless open – The file is fully protected when the device is locked, unless it was already open.
- complete until first user authentication – The file is fully protected until the user unlocks the device for the first time.
You should also be aware that this additional level of security is enabled by having a user passcode installed on the device. No passcode, no protection. That is the critical first step in enabling all of the above options. Also, the documentation leaves lots of questions as to what state a file will be in during the course of its life, and certainly what state it will be in when it leaves the device. To answer some of these questions I constructed a few tests. You may find the results surprising.
To begin with I created an SQlite database file and added a few records. I set the file protection level on this file to “complete” and then I locked the device.
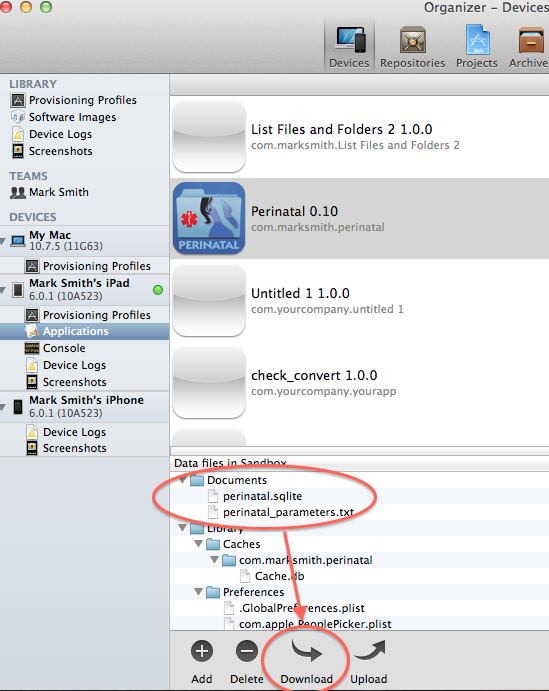
Next I used Xcode to transfer the file to my desktop. I was expecting to see an encrypted file but was surprised to see a blank one. Well, from a security perspective blank is good. No brute force attempts to decrypt it are possible. (Note: I have gotten different results using different versions of Xcode. Some return no file at all when the file is protected and the device is locked).
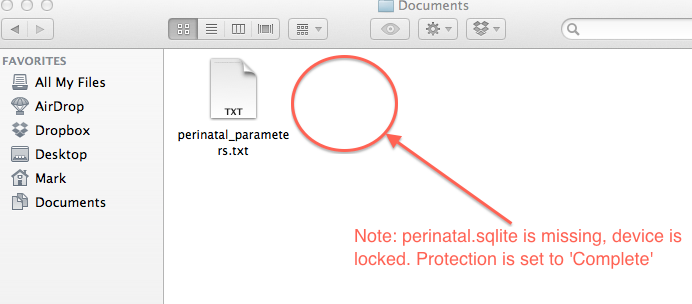
Then I unlocked the device and again transferred the file using Xcode, and as the documentation suggests, this file was completely readable. This is fine if you think no one can spy on your device while it’s unlocked, but what happens if the file is inadvertently backed up to iTunes or iCloud while the device is unlocked? Is the file protected in that case?
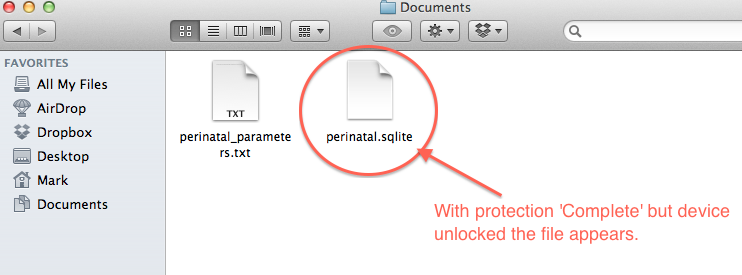
Well, in the case of iTunes the answer is “No”. The file is completely readable regardless of whether the device is locked or unlocked when the backup is made. Now, I was expecting the file to be readable when backed up from an unlocked device, but I was not expecting it to be readable when backed up from a locked device as well.
I suspect what is going on is that Apple treats a backup to a known trustworthy device the same as unlocking the device. You may recall when you first attempted to backup your device Apple asked you to enter the passcode. It probably stored it somewhere, and whenever the file is backed up again it uses that copy to decrypt the backup files.
In the case of backing up to iCloud, the Apple documentation says that all files backed up to iCloud are encrypted but my understanding is that the encryption is done with keys that are stored on the server side, so there is still a very small risk that someone hacking into Apple’s servers could discover both the keys and the files. However, given the sheer volume of backups that Apple maintains, there is some protection from the anonymity of being in such a large crowd.
So what have we learned? First, the iphoneSetFileDataProtection “complete” option appears to work to encrypt and secure the file when it is not being accessed. It is likely that the file is adequately protected until an authorized user (one who knows your passcode) requests access to the file. Second, it is not protected at all when backed up to iTunes. If that situation concerns you (or you don’t want the file backed up to iCloud), you have several options:
- Set the don’t backup flag on the file
- Put the file in a location that iTunes won’t back up
- Set iTunes to create encrypted backups (this is the only option for iCloud)
- Turn off iCloud backups
- Encrypt the file yourself
To set the file so it won’t be backed up use the iphoneSetDoNotBackupFile command with thedoNotBackup Boolean option (where true = do not backup):
To put the file in a location that iTunes won’t back up use either the /Library/Caches directory or the /Library/tmp directory. However, both of these locations can have files periodically removed by iOS to free up space, so they do not provide a solution for long term storage. The Apple recommended strategy is to mark the files as “do not backup”.
To create encrypted backups using iTunes, select the devices tab in iTunes and select your device. Then check the “Encrypt local backup option”. While you are there, you can also turn off iCloud backups by unchecking the “iCloud” option. Also, on your iOS device, using the “Settings” app you can disable iCloud backups under the iCloud/Storage and Backup option.
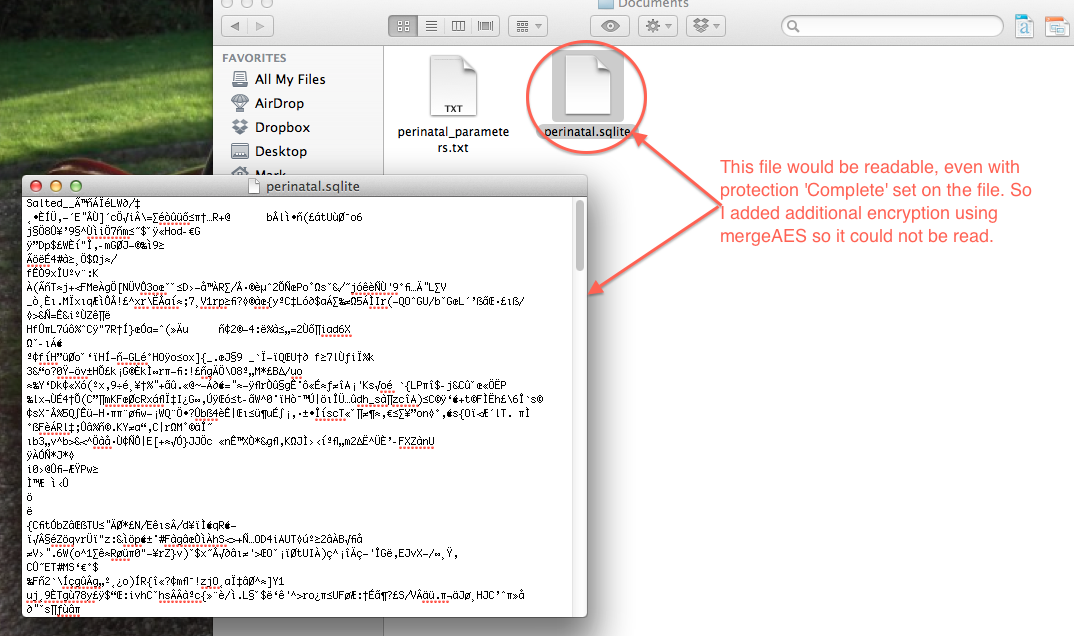
Of course there are other options as well. One is offered by Monte Goulding with his mergAES external for Livecode. I bought a copy of this to try out and I must say it has worked remarkably well for encrypting and decrypting the file on the fly on the iPad as well as ensuring that once the file leaves the iPad it remains encrypted (an added bonus frankly!). There is also an option in mergAES to encrypt the file in a format that is compatible with Livecode’s decryption routines (you need to use the OpenSSL format in mergAES).
Click image to zoom
Just don’t expect iphoneSetFileDataProtection to solve all of your security concerns unless you are only interested in protecting your files while they are “at rest” and you use a complex password on the device. If you really want the data to be secure you will probably have to double encrypt the file using something like mergAES. That way, if someone is really determined to get at your data they will find that after circumventing the first hurdle (your passcode) they are still left with a securely encrypted file.
Of course there is lots more to iOS file and application security than what I’ve covered here. Recently I ran across a new publication by Apple that appears to cover the iOS security issues in much more detail than has previously been reported (it’s 20 pages in length). As of Dec 8th, 2012 you could find the document here.
(NOTE: as of January 4, 2013 this document is no longer available or is encrypted. If anyone wants a copy please request in the comment box below).
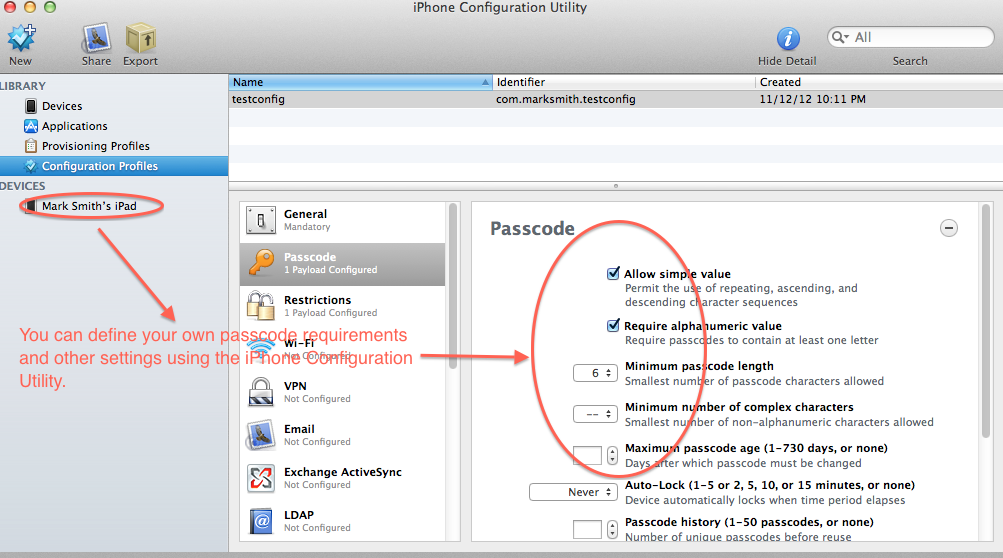
Finally, if you are handing out iOS devices, you may want to consider enforcing the use of a complex passcode as well as other security settings. You can do this by creating a configuration profile for the device. I don’t have the space here to go into this in any detail but luckily Apple has a tool you can use (the iPhone Configuration Utility) that will work on any iOS device and it has excellent documentation.
Click image to zoom
The Configuration Utility is available here.
The only solution I can think of that would be better is to have encryption built right in to the SQlite library (there is such a package, but it is not licensed by Runrev. If you think you would use this you might want to send RunRev a note sometime to let them know). Well, that’s it for me. As you travel down your “mobile” path in life may your data always be secure.

12 Quick Tips to Search Google like an Expert
by Arnaud on January 18, 2013 1 commentBy Dharmesh Shah at Hubspot
If you’re like me, you probably use Google many times a day. But, chances are, unless you are a technology geek, you probably still use Google in its simplest form. If your current use of Google is limited to typing a few words in, and changing your query until you find what you’re looking for, then I’m here to tell you that there’s a better way – and it’s not hard to learn. On the other hand, if you are a technology geek, and can use Google like the best of them already, then I suggest you bookmark this article of Google search tips. You’ll then have the tips on hand when you are ready to pull your hair out in frustration when watching a neophyte repeatedly type in basic queries in a desperate attempt to find something.
By learning and using the 12 tips below, you’ll rank up there with the best of the Google experts out there. I’ve kept the descriptions of the search tips intentionally terse as you’re likely to grasp most of these simply by looking at the example from Google anyways.
12 Expert Google Search Tips
- Explicit Phrase:
Lets say you are looking for content about internet marketing. Instead of just typing internet marketing into the Google search box, you will likely be better off searching explicitly for the phrase. To do this, simply enclose the search phrase within double quotes.
Example: “internet marketing”
- Exclude Words:
Lets say you want to search for content about internet marketing, but you want to exclude any results that contain the term advertising. To do this, simply use the “-” sign in front of the word you want to exclude.
Example Search: internet marketing -advertising
- Site Specific Search:
Often, you want to search a specific website for content that matches a certain phrase. Even if the site doesn’t support a built-in search feature, you can use Google to search the site for your term. Simply use the “site:somesite.com” modifier.
Example: “internet marketing” site:www.smallbusinesshub.com
- Similar Words and Synonyms:
Let’s say you want to include a word in your search, but want to include results that contain similar words or synonyms. To do this, use the “~” in front of the word.
Example: “internet marketing” ~professional
- Specific Document Types:
If you’re looking to find results that are of a specific type, you can use the modifier “filetype:”. For example, you might want to find only PowerPoint presentations related to internet marketing.
Example: “internet marketing” filetype:ppt
- This OR That:
By default, when you do a search, Google will include all the terms specified in the search. If you are looking for any one of one or more terms to match, then you can use the OR operator. (Note: The OR has to be capitalized).
Example: internet marketing OR advertising
- Phone Listing:
Let’s say someone calls you on your mobile number and you don’t know who it is. If all you have is a phone number, you can look it up on Google using the phonebook feature.
Example: phonebook:617-555-1212 (note: the provided number does not work – you’ll have to use a real number to get any results).
- Area Code Lookup:
If all you need to do is to look-up the area code for a phone number, just enter the 3-digit area code and Google will tell you where it’s from.
Example: 617
- Numeric Ranges:
This is a rarely used, but highly useful tip. Let’s say you want to find results that contain any of a range of numbers. You can do this by using the X..Y modifier (in case this is hard to read, what’s between the X and Y are two periods.) This type of search is useful for years (as shown below), prices, or anywhere where you want to provide a series of numbers.
Example: president 1940..1950
- Stock (Ticker Symbol):
Just enter a valid ticker symbol as your search term and Google will give you the current financials and a quick thumb-nail chart for the stock.
Example: GOOG
- Calculator:
The next time you need to do a quick calculation, instead of bringing up the Calculator applet, you can just type your expression in to Google.
Example: 48512 * 1.02
- Word Definitions:
If you need to quickly look up the definition of a word or phrase, simply use the “define:” command.
Example: define:plethora
Hope this list of Google search tips proves useful in your future Google searches. If there are any of your favorite Google expert power tips that I’ve missed, please feel free to share them in the comments.

Digital Archaeology of Computing and IT
by Arnaud on January 11, 2013 1 commentBy Heather Laine
 A recent newsletter article in revUp got me thinking about this topic. It seems extraordinary that already, in just 20 or 30 years, we can be using the word archaeology in connection with computing and IT technology. Surely it’s too soon? We all know what a floppy disc is, don’t we? We remember those 128k Desktop Computers that required a reinforced desk to put them on and a second mortgage to purchase them? I don’t know about you, but I’m certainly not a dinosaur yet!
A recent newsletter article in revUp got me thinking about this topic. It seems extraordinary that already, in just 20 or 30 years, we can be using the word archaeology in connection with computing and IT technology. Surely it’s too soon? We all know what a floppy disc is, don’t we? We remember those 128k Desktop Computers that required a reinforced desk to put them on and a second mortgage to purchase them? I don’t know about you, but I’m certainly not a dinosaur yet!
And yet…
There is a beautiful mountain walk near where I live, up a valley which used to be a big industrial site. You’d never think it now, until you reach the end of the path, and you see a tall factory chimney rising out of a quiet sheep covered moorland. Nearby are some old workings and a tourist board notice. The board dates the workings to the late 1800s. It says, “It is thought the chimney was associated with ventilation for the mine…” What? This is only a hundred or so years ago, and we don’t know what it was for? I guess everybody thought Tom was writing it down…

Around the world there are millions of floppy discs and even older media quietly rotting in landfill sites, cellars, attics and forgotten cupboards. I have a bunch of them myself, and I certainly no longer have any kind of computer that could run them. That data is gone as far as I am concerned. Hope it wasn’t important!
 There is a vast store of data out there, on somewhat perishable media, and within a few years there will be virtually no machines left capable of reading it. Most of it undoubtedly is dross but there must be a huge body of work worth saving.
There is a vast store of data out there, on somewhat perishable media, and within a few years there will be virtually no machines left capable of reading it. Most of it undoubtedly is dross but there must be a huge body of work worth saving.
With the advent of Mobile, many games that were written for what today are regarded as extremely low spec machines have a new venue. Mobile devices need games that pay some attention to size and speed, offering a home to those much loved games you played way back when 128k was a lot of memory.
Perhaps even more transient and in need of preservation are historic and ground breaking websites. Do you remember your first web browsing experience? Come a long way since then, haven’t we! I vividly remember the hamster dance, possibly one of the earliest internet memes. I was mesmerised – I’d never seen anything like it. It was a big step along the road to making websites move and sing, and it would be a huge shame if the youth of today could not experience the joy of 4 repeating hamsters cycling through 4 gif images to a sped up Disney tune! When I came to hunt for the link for this article however, it was not easy to find anything resembling the original.
The hamsterdance.com site is now a sleek modern version with merchandise galore (and to my mind totally lacking the charm of the original). The link I did find for you is a reconstruction. Unlike books, websites leave no physical trace when they are overwritten or erased, and unless consideration is given now to preserving and recording the history of the internet, much will be completely lost.
Do we care? Should we care? Obviously we cannot and probably should not attempt to preserve everything. But if in 50 years’ time little Johnny in his digital immersion world holotexts his grandma to ask “How did the internet get the way it is today?” I think it would be a good thing to be able to answer that question.


Recent Comments